Active Directory Service Accounts: A closer look at one of the most common NHIs and their role in lateral movement
The security of Non-Human Identities (NHIs) is now top of mind for security stakeholders. But what exactly is a non-human identity, and how do they impact an organization’s cybersecurity posture? NHI is a broad term used to describe when a machine, application, or service is given credentials to perform an automated task or action. There are many types of NHIs, including API keys, service accounts, system accounts, OAuth tokens, amongst others. Let’s say IT manager Bob writes a script asking a machine to perform a daily backup to a server. Bob is giving the machine credentials and access to perform the automated backup. This is an NHI.
In today’s research, we’re going to zero in on the most prevalent and regularly compromised type of NHI: Active Directory service accounts. Within the large pool of NHI types, service accounts — used for machine-to-machine communication within Microsoft’s Active Directory’s (AD) environments — are the most concerning. These identities are just as vulnerable to potential compromise and abuse than human ones. In fact, due to historic lack of visibility and protection, they might even be at graver risk. Typically, they have privileged access to sensitive machines, effectively making them admin accounts.
We’ve uncovered data from the past 12 months that helps us answer those questions. In our research, we unpack the scope of AD service accounts, their compromise exposure, and the confidence of identity security teams in their ability to discover and protect them.
Why NHIs — AD Service Accounts — are an Attacker’s Best Friend
By default, attackers will target service accounts for lateral movement due to their high-access privileges, low visibility, and protection challenges. And, in many cases, service accounts fly under the radar of security and identity teams because they don’t even know they exist. Using the same example as above, when IT manager Bob automates the backup of a server but then leaves the company, that automated machine-to-machine task continues unseen and unmonitored. The service account still has access to both the server and the backup server, making it an enticing target for a bad actor.
The risks associated with a breached service account are immense because it can lead to the compromise of the organization’s entire SaaS environment, too. Even though service accounts are not supposed to be synced from AD to the cloud identity provider (IdP), it’s extremely common for identity teams to sync them inadvertently. While these accounts can’t be used to access SaaS resources by default, an attacker that has gained admin access privileges to the cloud IdP can activate them and assign them access privileges.
Sample attack flow:
- Attacker gains admin access privileges to the cloud IdP management console.
- Once inside, the attacker searches for synced service accounts (naming conventions are a useful guide) until finding one.
- Attacker configures an access policy for the chosen service account and assigns it access privileges to SaaS apps.
- Attacker then uses the service account to access and act within the SaaS environment.
The Sheer Volume of AD Service Accounts Is Alarming
Service accounts make up a large portion of total users within a company’s AD
On average, around one-third of users within AD are service accounts. The ratio of service accounts to total identities in larger companies is smaller, but that doesn’t mean they have fewer service accounts when it comes to absolute value. To put this into context, a large enterprise with 100,000 users in AD would likely have approximately 23,000 active service accounts.
In smaller organizations, nearly half of all AD users are service accounts with high privileges and access.
Service Accounts’ Exposure to Compromise
Weak authentication protocols make service accounts vulnerable
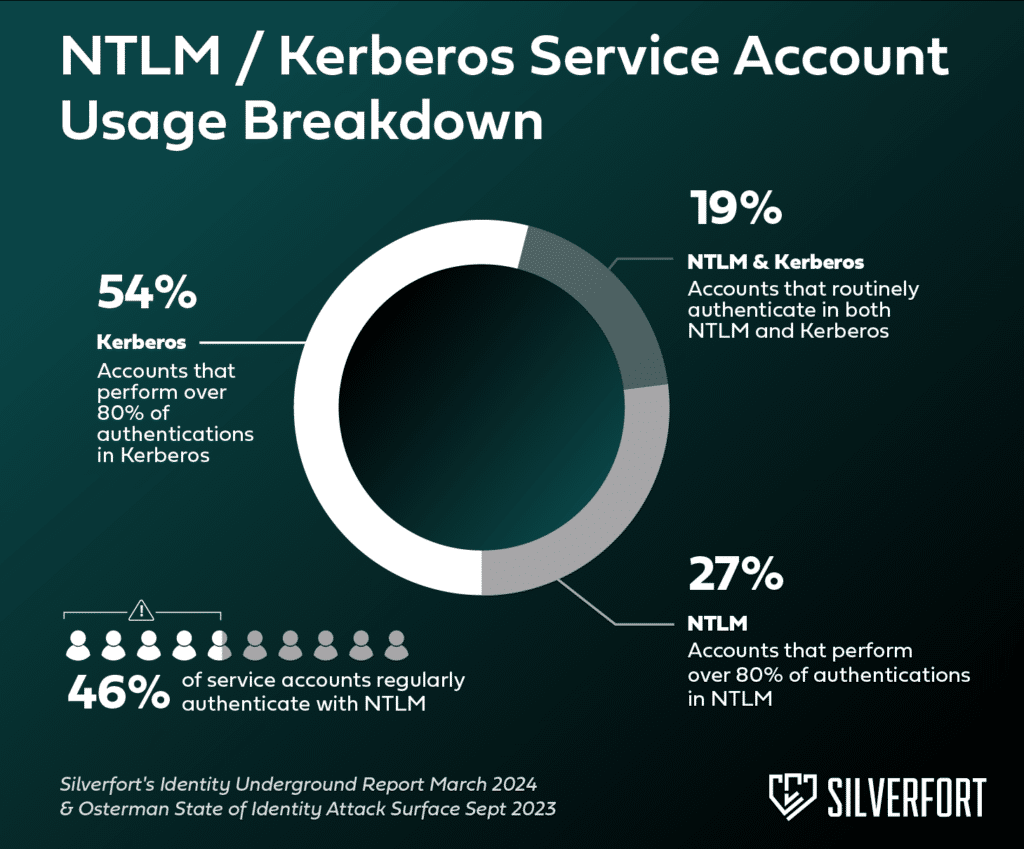
NTLM still exists in many Windows domains despite being a very weak authentication protocol that’s susceptible to credential access and lateral movement. In fact, 46% of service accounts regularly authenticate via this deprecated protocol, leaving them more exposed to compromise.
Visibility into Service Accounts is Murky at Best
Teams aren’t so sure they have an accurate inventory of service accounts
Complete visibility into all your human and non-human identities is fundamental to good identity security. Yet a recent whitepaper by Osterman Research revealed that only 5.7% of organizations have full visibility into their service accounts, while 62% only have partial visibility.
Most NHIs, including service accounts, cannot be protected with MFA, and the lack of visibility into their activities eliminates the possibility of protecting them in a Privileged Access Management (PAM) vault with password rotation.
Confidence in Protecting Service Accounts is Minimal
Protection of service accounts is a serious challenge for organizations
Only 1 in 5 organizations are highly confident that they can prevent adversaries from using a service account for malicious access. This leaves 80% of organizations unable to prevent the misuse of service accounts in real time due to sporadic or absent visibility and security.
Lateral movement continues to be a thorn in the defender’s side
Moving laterally through an organization is table stakes for an attacker, and service accounts are one of their top targets to do so. Alarmingly, only 22.4% of organizations are confident they can stop lateral movement with compromised credentials in their environments.
Looking Ahead: NHIs Present a Challenge, But There Are Solutions
NHIs make up a significant portion of an organization’s total identities. The volume of NHIs will continue to climb as we accelerate the pace of automation, innovation, and the great amplifier — artificial intelligence. Today, we analyzed a single type of NHI used at the typical organization, but it’s not hard to imagine a slew of similar results if we expanded our scope and applied the analysis to other types of NHIs regularly used at organizations globally. The compromise of a single NHI service account could give attackers access to multiple resources, making it an ideal target for attackers — sophisticated or not. And they’ll rarely face much resistance, as standard security controls like traditional MFA can typically only protect human identities.
Coupled with the fact that only one in five organizations is highly confident in preventing identity threats, this paints an alarming picture.
Steps to protecting your non-human identities
1. Strive for least privilege: Limit access at the most granular level, especially on privileged non-human accounts, based on source, destination, protocol, time, and other factors. Excessive privileges can lead to unintentional risks in an organization such as data loss or theft, as well as creating more and unnecessary targets for phishing attacks.
2. Define your “normal”: To establish a risk, or what’s deemed abnormal activity in a network, clearly establish a baseline of what “normal” behavior looks like for all identities, both human and non-human. This should be particularly easy for service accounts, whose behavior is highly predictable and repetitive – assuming, of course, you already have visibility into your NHIs.
3. Quickly spot abnormal activity: With the right tools in place to proactively monitor and alert them to these abnormal activities, teams can then respond quickly. This helps identify and prevent any further deviations, and if attackers are trying to break into the network, the security team can efficiently mitigate and contain the scope of their attack .
4. Automatically block atypical service accounts’ access attempts: Detection is not enough. You should also be able to actively block a suspected compromised service account from accomplishing access to the targeted resource.
5. Seek out a tool that extends MFA beyond human identities. MFA is a tried and tested security control that has proven time and again to thwart attackers. By extending MFA to resources that were once unprotectable, you finally conduct a “double check” on every authentication request — even for NHIs. Learn more about how Silverfort can help protect your NHIs.
Report Methodology
In Silverfort’s Identity Underground Report, we looked at hundreds of thousands of data points across hundreds of customers of different sizes and verticals to determine the scope of the non-human identity problem, with a focus on highly privileged and pervasive Active Directory service accounts.
We also conducted research with Osterman Research, which included responses from 637 people in identity roles during May-June 2023. To qualify, respondents had to work at organizations with at least 1,000 employees. The surveys were conducted in six countries, with the surveys in France and Germany fielded in French and German respectively. The survey was cross industry, and no industries were excluded or restricted.